Is your company prepared to shell out millions of dollars to combat a cyberattack? It’s not just the major players who are getting hacked. Cybercriminals have expanded their arsenal and protection is becoming harder and harder to achieve.
Ransomware attacks rose by 150% in 2021, and that trend will continue in the last quarter of 2022 and into 2023.
High-profile victims like Colonial Pipeline and Solar Winds have had to remit millions in ransom payments to cybercriminal groups like DarkSide and BlackMatter. These cybercriminals are reinvesting their gains, resulting in bigger budgets for their future attacks.
With malware evolving, it’s more vital than ever that organizations stay up to date on the latest cybersecurity threats. Who are the top perpetrators and what can you do to ensure your safety? We will be delving into the current state of cybersecurity in a two-part series on the top trends in ransomware and how to protect your organization from cyber threats.
Check out our rundown below on the rise of ransomware in 2022.
THE EVOLUTION OF RANSOMWARE

Ransomware is typically defined as a threat actor using malware to encrypt files on a victim’s computer and only decrypting them in exchange for a sum of money. Their techniques have evolved over the years.
For example, double extortion techniques have become the norm, in which the hacker both encrypts data to prevent users from accessing it and steals the data with the intent to release it if the victim does not pay up. Hackers can threaten to leak industry secrets, intellectual property, or corporate dirty laundry if their targets do not pay the ransom.
HOW MALWARE EVADES CYBERSECURITY SOFTWARE
Speed is key. If protection software catches malware early on, it can mitigate the damage. One of the ways in which ransomware actors can accelerate their programs is by employing a partial encryption scheme. These schemes only encrypt part of the file rather than the whole thing. This shortens the attack duration while achieving the same effect of encrypting sensitive information. Protection software often can’t keep up and detect the malware in time to save files from becoming inaccessible.
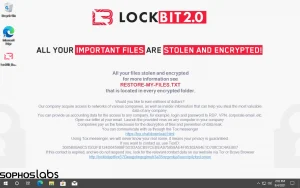
Ransomware actors will compete to get the best criminal hacker talent. They also try to find corporate insiders who will give them access to the inside of major organizations. For example, Lockbit 2.0 set the message below to a user’s wallpaper, offering millions of dollars to give access to insider information:
BLACKMATTER RANSOMWARE
On Friday May 7th, 2021, Colonial Pipeline was hit with a ransomware attack by DarkSide, a Ransomware-as-a-Service (RaaS) organization. The attack was highly successful in disrupting the major US fuel pipeline’s operations. Consequentially, DarkSide shut down as its servers were seized and its cryptocurrency wallets drained.
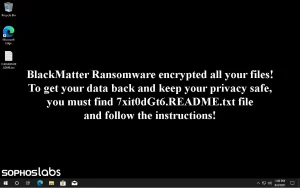
In the wake of that event, BlackMatter emerged, claiming to fill the void left by what was one of the elite ransomware organizations. BlackMatter adopted the best tools and techniques from a mix of LockBit, DarkSide and REvil. BlackMatter immediately sets a wallpaper that’s very similar to DarkSide’s which informs the user that all their files are encrypted (see below).
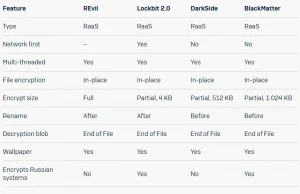
Analysis shows that the code to BlackMatter is similar, but not identical to DarkSide. HC3 claims the group is Russian speaking and likely Eastern European. Its targeted countries include the US, India, Brazil, Chile and Thailand. Cybersecurity firm Sophos Labs included a detailed breakdown of the various similarities between BlackMatter and its predecessors in the table below:
IS YOUR ORGANIZATION VULNERABLE?
Cybercrime is at an all-time high. Is your organization vulnerable? Furthermore, how can you protect your company?
A report by SonicWall found that out of the top 10 countries for ransomware volume, the US had nearly four times as many attacks as the other nine countries put together.
The security firm Kela discovered that cybercriminals use analytics to identify the ideal US victim. They are specifically hunting for companies with over $100 million in revenue that are using private networks, remote desktop protocols or tools from Citrix, VMware, Cisco, Palo Alto Networks, and Fortinet. The most targeted industry in 2021 has been government—government organizations saw 10 times more attacks than average in mid-2021.
It was previously thought that these hackers were inclined to shy away from organizations in education, healthcare, or the non-profit sector because they don’t have the budget to pay or can cause a backlash against the hacking group. However, hackers recently targeted LA School District, exposing more than 400,000 students, faculty and staff. With unscrupulous attacks like this on the rise, it appears no one is safe.
HOW CAN YOU PROTECT YOUR COMPANY?
In our next blog, we will explore the best cybersecurity practices you can implement to protect your company from hackers.

